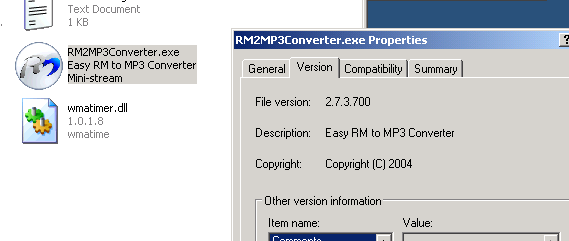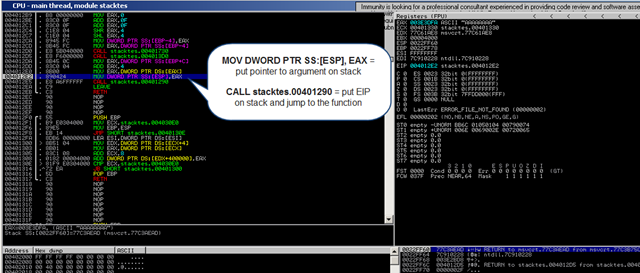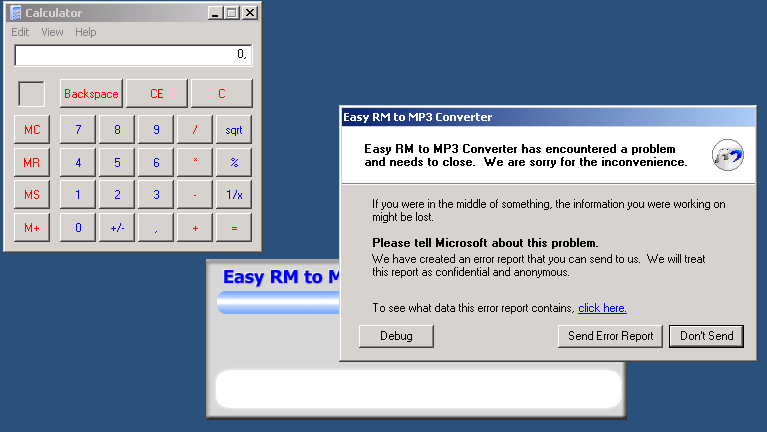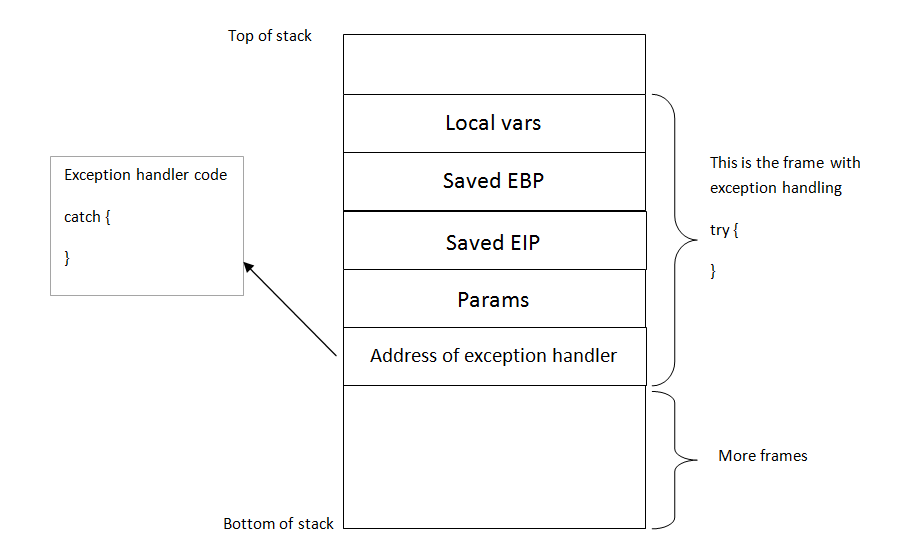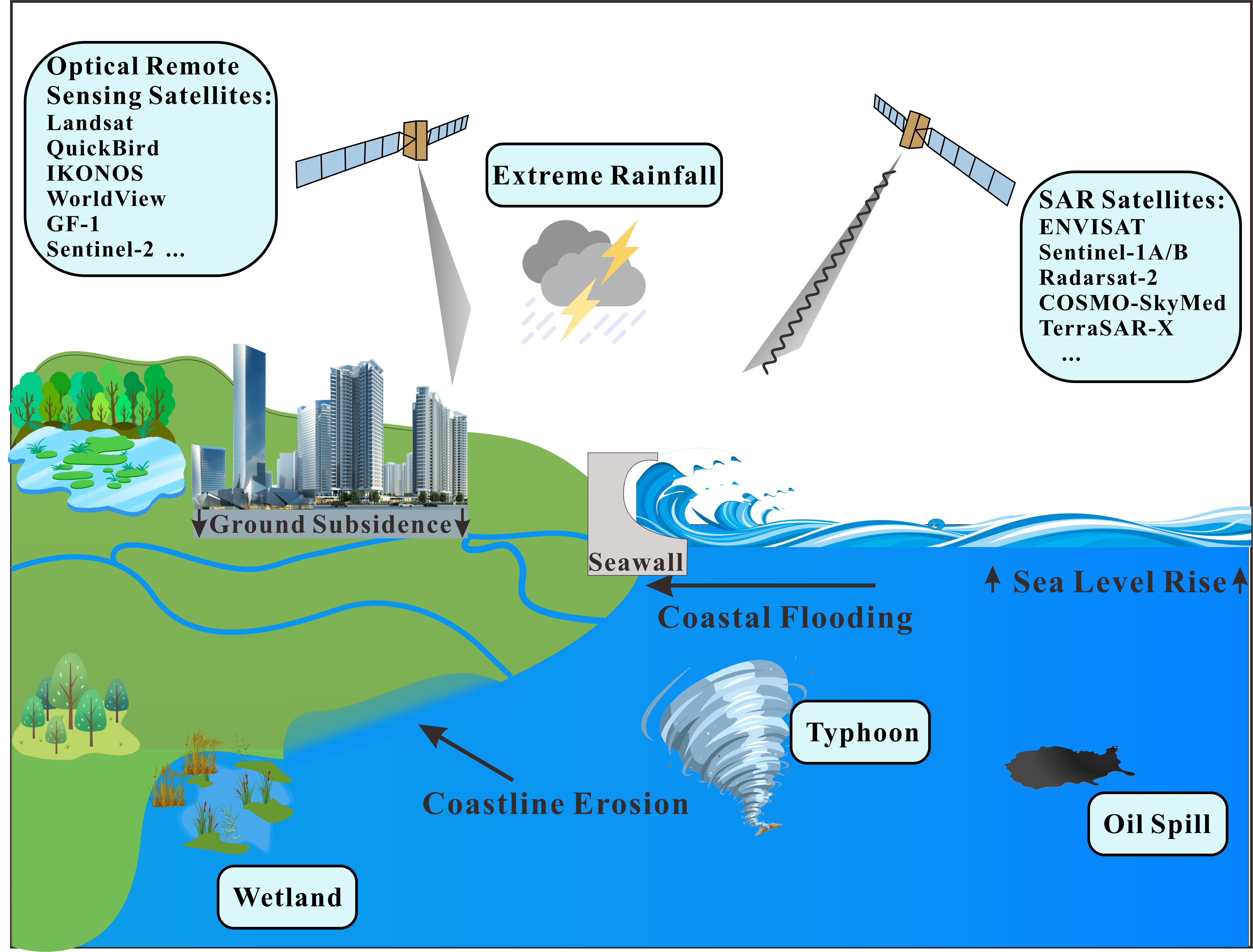
Remote Sensing | Free Full-Text | On the Exploitation of Remote Sensing Technologies for the Monitoring of Coastal and River Delta Regions

Recent Advances in the Development of Sigma Receptor Ligands as Cytotoxic Agents: A Medicinal Chemistry Perspective | Journal of Medicinal Chemistry